AZ-104: Microsoft Azure Administrator
You have an Azure subscription that contains 10 virtual networks. The virtual networks are hosted in separate resource groups.
Another administrator plans to create several network security groups (NSGs) in the subscription.
You need to ensure that when an NSG is created, it automatically blocks TCP port 8080 between the virtual networks.
Solution: From the Resource providers blade, you unregister the Microsoft.ClassicNetwork provider.
Does this meet the goal?
Yes
No
Answer is No
You need to use a custom policy definition, because there is not a built-in policy.
Resource policy definition used by Azure Policy enables you to establish conventions for resources in your organization by describing when the policy is enforced and what effect to take. By defining conventions, you can control costs and more easily manage your resources.
Reference:
https://docs.microsoft.com/en-us/azure/azure-policy/policy-definition
https://docs.microsoft.com/en-us/azure/governance/policy/samples/built-in-policies
You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains the users shown in the following table:
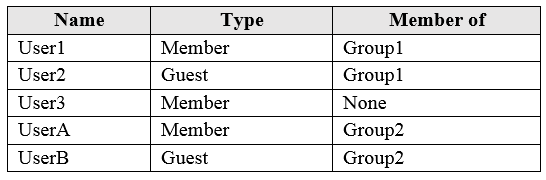
User3 is the owner of Group1.
Group2 is a member of Group1.
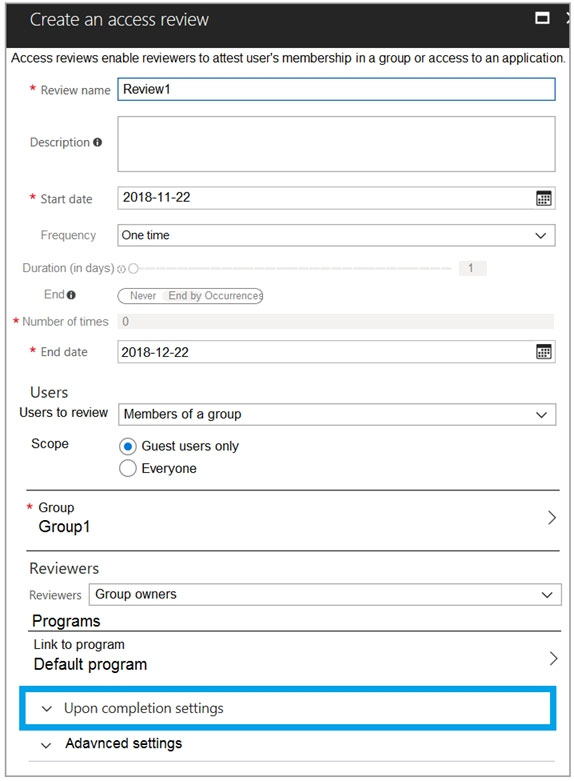
You configure an access review named Review1 as shown in the following exhibit:
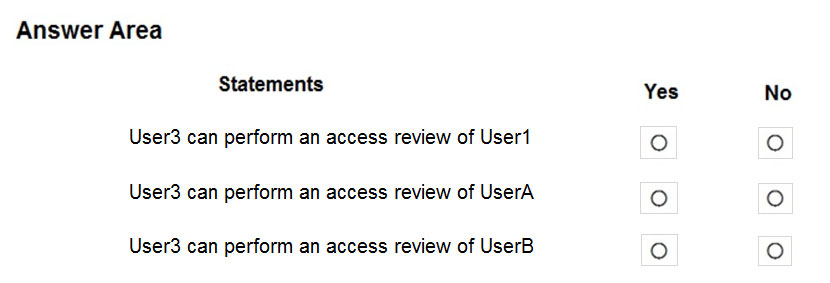
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
Box 1: No
User 3 can only review guest users, and User1 is a member user.
Box 2: No
User 3 can only review guest users, and User2 is a member user.
Box 3: Yes
Group2 is a member of Group1 and User3 is the owner of this group, therefore everyting included in Group2 can be reviewed by User3.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/governance/create-access-review
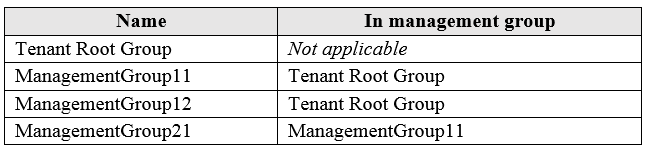
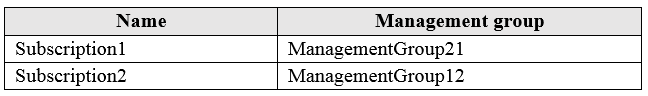
You have the Azure management groups shown in the following table:
You add Azure subscriptions to the management groups as shown in the following table:
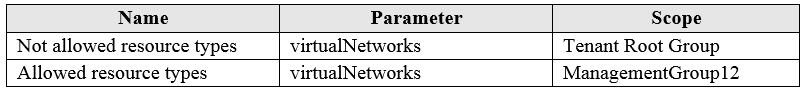
You create the Azure policies shown in the following table:
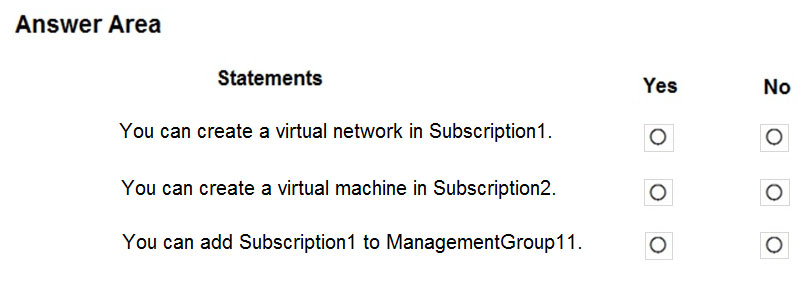
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
Allowed Resource Type (Deny): Defines the resource types that you can deploy. Its effect is to deny all resources that aren't part of this defined list.
Not allowed resource types (Deny): Prevents a list of resource types from being deployed.
Based on the Policies, VNETs are not allowed in the Tenant Root Group scope, so you cannot deploy VNETs. Also, VNETs only allowed in ManagementGroup12 scope, but you cannot deploy any other resource.
Box 1: No
Subscription1 is a member of ManagementGroup21, ManagementGroup21 is a member of ManagementGroup11, ManagementGroup11 is a member of the Tenant Root Group, The Tenant Root group has 'Not allowed resource types for virtual network'.
Box 2: No:
You cannot create a VM, because based on the Policy you can only create VNETs in Sybscription2 (ManagementGroup12).
Box 3: No
You cannot ADD Subscription1 to ManagementGroup11, but you can MOVE Subscription1 from ManagementGroup21 to ManagmentGroup11. Subscriptions can only be a member of ONE ManagementGroup at a time.
Reference:
https://docs.microsoft.com/en-us/azure/governance/management-groups/overview
https://docs.microsoft.com/en-us/azure/governance/management-groups/manage#moving-management-groups-and-subscriptions
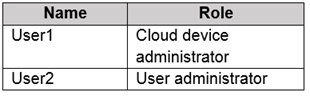
You have Azure Active Directory tenant named Contoso.com that includes following users:
Contoso.com includes following Windows 10 devices:
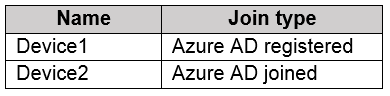
You create following security groups in Contoso.com:

For each of the following statements, select Yes if the statement is true. Otherwise, select No.
Box 1: No
Cloud administrators can manage devices, not group membership. Group1 is also an Assigned Group.
Box 2: Yes
User administrators can manage all aspects of Security Groups. Group1 is also an Assigned Group.
Box 3: No
Dynamic membership. You cannot add Members to Dynamic Groups. Group 2 is a Dynamic Group, so you cannot add devices or users to dynamic groups. Dynamic groups can only add members by a defined rule.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/roles/permissions-reference
https://docs.microsoft.com/en-us/azure/active-directory/enterprise-users/groups-dynamic-membership
You have an Azure subscription that contains a virtual network named VNET1 in the East US 2 region. A network interface named VM1-NI is connected to VNET1.
You successfully deploy the following resources in an Azure Resource Manager template.
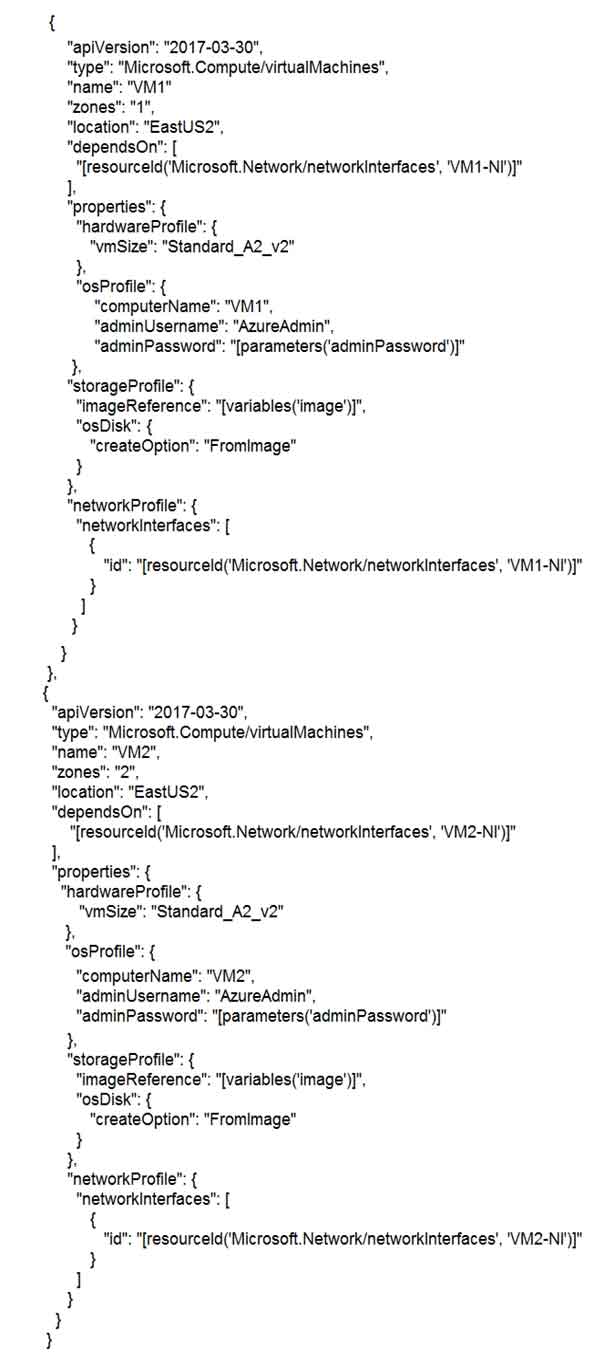
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
Box 1: Yes
VNET1 is in the same region as VM1 and VM2, so it can connect with both.
Box 2: Yes
Because both VMs are in different Availability Zone, hence either one would be available if one Data Center fails.
Box 3: No
If the Region fails then both VMs, which are present in the Region will not be available.
Reference:
https://docs.microsoft.com/en-us/azure/architecture/resiliency/recovery-loss-azure-region
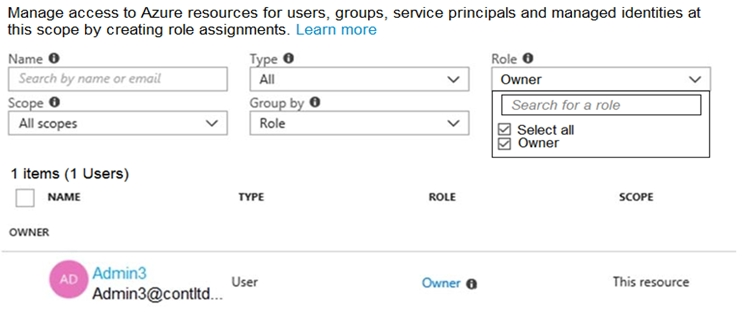
You have an Azure Active Directory (Azure AD) tenant that contains three global administrators named Admin1, Admin2, and Admin3.
The tenant is associated to an Azure subscription. Access control for the subscription is configured as shown in the Access control exhibit.
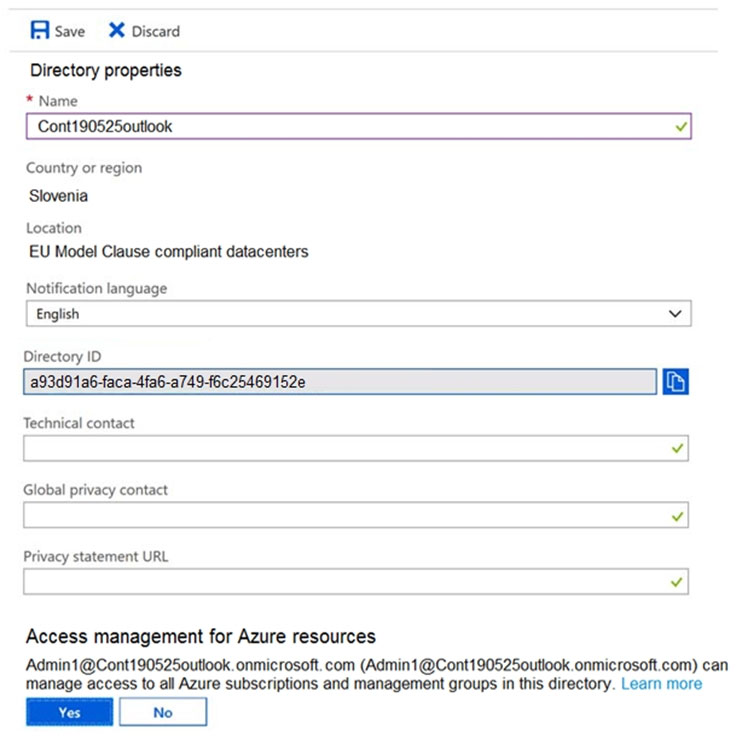
You sign in to the Azure portal as Admin1 and configure the tenant as shown in the Tenant exhibit.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
Azure (RBAC) and Azure AD roles are independent. AD roles do not grant access to resources and Azure roles do not grant access to Azure AD. However, a Global Administrator in AD can elevate access to all subscriptions and will be User Access Administrator in Azure root scope.
All 3 users are GA (AD) and Admin3 is owner of the subscription (RBAC).
Admin1 has elevated access, so he is also User Access Admin (RBAC).
To assign a user the owner role at the Subscription scope, you require permissions, such as User Access Admin or Owner.
Box 1: Yes
Admin1 has elevated access, so he is User Access Admin. This is valid.
Box 2: Yes
Admi3 is Owner of the Subscription. This is valid.
Box 3: No
Admin2 is just a GA in Azure AD scope. He doesn’t have permission in the Subscription.
Reference:
https://docs.microsoft.com/en-us/azure/role-based-access-control/elevate-access-global-admin
https://docs.microsoft.com/en-us/azure/role-based-access-control/role-assignments-portal-subscription-admin
You have an Azure subscription that contains the resources shown in the following table.
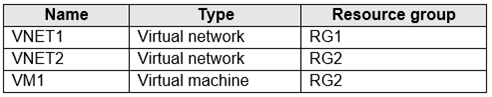
The status of VM1 is Running.
You assign an Azure policy as shown in the exhibit.
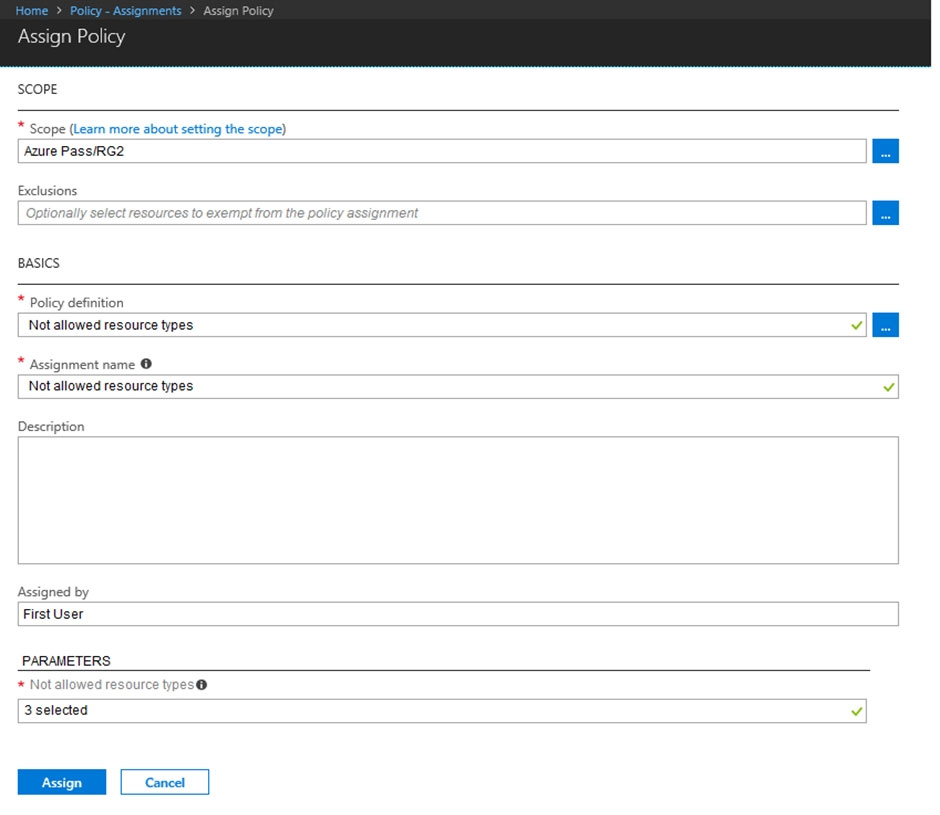
You assign the policy by using the following parameters:
- Microsoft.ClassicNetwork/virtualNetworks
- Microsoft.Network/virtualNetworks
- Microsoft.Compute/virtualMachines
For each of the following statements, select Yes if the statement is true. Otherwise, select No.

Existing non-compliant resources can be remediated with a remediation task. But no action is taken against them other than to mark them as non-compliant.
Box 1: Yes
You can move already existing VNETs to the RG applying this policy.
Box 2: No
Existing resources are not modified by newly created policies. VM will stay as is.
Box 3: No
New changes to existing resources will have to be compliant with the policies applying the RG, so no new changes will be allowed to existing VNETs.
You have Azure subscription that includes following Azure file shares:

You have the following on-premises servers:
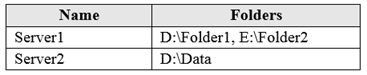
You create a Storage Sync Service named Sync1 and an Azure File Sync group named Group1. Group1 uses share1 as a cloud endpoint.
You register Server1 and Server2 in Sync1. You add D:Folder1 on Server1 as a server endpoint of Group1.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
Box 1: No
Group1 already has a cloud endpoint named Share1.
A sync group must contain one cloud endpoint, which represents an Azure file share and one or more server endpoints.
Box 2: Yes
Yes, one or more server endpoints can be added to the sync group.
Box 3: Yes
Yes, one or more server endpoints can be added to the sync group.
Reference:
https://docs.microsoft.com/en-us/azure/storage/files/storage-sync-files-deployment-guide
You have a sync group named Sync1 that has a cloud endpoint. The cloud endpoint includes a file named File1.txt.
Your on-premises network contains servers that run Windows Server 2016. The servers are configured as shown in the following table.
You add Share1 as an endpoint for Sync1. One hour later, you add Share2 as an endpoint for Sync1.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.

Answer is NO, NO, YES:
Azure File Sync uses a simple conflict-resolution strategy: we keep both changes to files that are changed in two endpoints at the same time.
The most recently written change keeps the original file name. The older file (determined by LastWriteTime) has the endpoint name and the conflict number appended to the filename. For server endpoints, the endpoint name is the name of the server. For cloud endpoints, the endpoint name is Cloud. The name follows this taxonomy:
(FileNameWithoutExtension)-(endpointName)[-#].
Reference:
https://docs.microsoft.com/en-us/azure/storage/files/storage-sync-files-planning
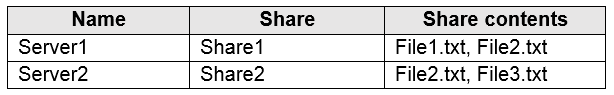
You have an Azure subscription that contains the file shares shown in the following table.
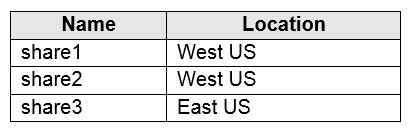
You have the on-premises file shares shown in the following table.
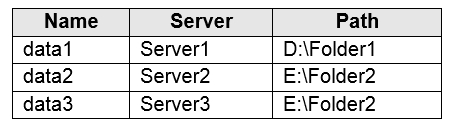
You create an Azure file sync group named Sync1 and perform the following actions:
- Add share1 as the cloud endpoint for Sync1.
- Add data1 as a server endpoint for Sync1.
- Register Server1 and Server2 to Sync1.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
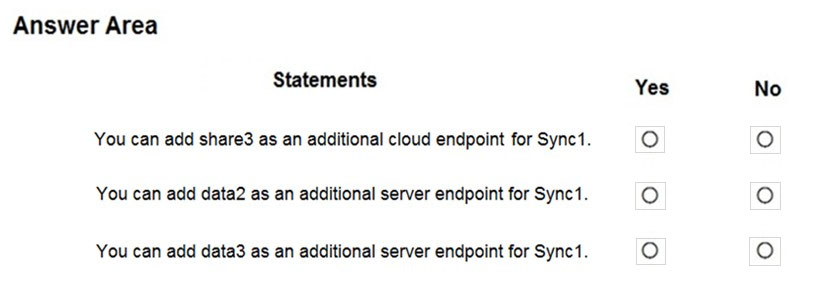
Box 1: No
A sync group must contain one cloud endpoint, which represents an Azure file share and one or more server endpoints.
Box 2: Yes
Data2 is located on Server2 which is registered to Sync1.
Box 3: No
Data3 is located on Server3 which is not registered to Sync1.
Reference:
https://docs.microsoft.com/en-us/azure/storage/files/storage-sync-files-deployment-guide?tabs=azure-portal%2Cproactive-portal#create-a-sync-group-and-a- cloud-endpoint