AZ-900: Microsoft Azure Fundamentals
Where can a legal team access information around how the Microsoft cloud helps them secure sensitive data and comply with applicable laws and regulations?
Microsoft Privacy Statement
Trust Center
Online Services Terms
Answer is Trust Center
The Trust Center is a great resource for people in your organization who might play a role in security, privacy, and compliance.
Where can the IT department find reference blueprints that it can apply directly to its Azure subscriptions?
Online Services Terms
Azure compliance documentation
Microsoft Privacy Statement
Answer is Azure compliance documentation
The compliance documentation provides reference blueprints, or policy definitions, for common standards that you can apply to your Azure subscription.
To complete the sentence, select the appropriate option in the answer area.
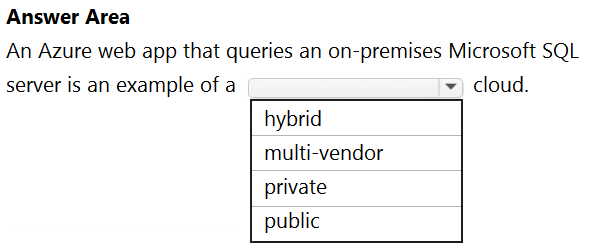
hybrid
multi-vendor
private
public
Answer is hybrid
Reference:
https://azure.microsoft.com/en-gb/overview/what-is-hybrid-cloud-computing/
You have 1,000 virtual machines hosted on the Hyper-V hosts in a data center.
You plan to migrate all the virtual machines to an Azure pay-as-you-go subscription.
You need to identify which expenditure model to use for the planned Azure solution.
Which expenditure model should you identify?
operational
elastic
capital
scalable
Answer is operational
One of the major changes that you will face when you move from on-premises cloud to the public cloud is the switch from capital expenditure (buying hardware) to operating expenditure (paying for service as you use it). This switch also requires more careful management of your costs. The benefit of the cloud is that you can fundamentally and positively affect the cost of a service you use by merely shutting down or resizing it when it's not needed.
Reference:
https://docs.microsoft.com/en-us/azure/architecture/cloud-adoption/appendix/azure-scaffold
You need to identify the type of failure for which an Azure Availability Zone can be used to protect access to Azure services.
What should you identify?
a physical server failure
an Azure region failure
a storage failure
an Azure data center failure
Answer is an Azure data center failure
Availability zones expand the level of control you have to maintain the availability of the applications and data on your VMs. An Availability Zone is a physically separate zone, within an Azure region. There are three Availability Zones per supported Azure region.
Each Availability Zone has a distinct power source, network, and cooling. By architecting your solutions to use replicated VMs in zones, you can protect your apps and data from the loss of a datacenter. If one zone is compromised, then replicated apps and data are instantly available in another zone.
Reference:
https://docs.microsoft.com/en-us/azure/virtual-machines/availability
Your company plans to migrate to Azure. The company has several departments. All the Azure resources used by each department will be managed by a department administrator.
What are two possible techniques to segment Azure for the departments?
multiple subscriptions
multiple Azure Active Directory (Azure AD) directories
multiple regions
multiple resource groups
Answers are multiple subscriptions
multiple resource groups
An Azure subscription is a container for Azure resources. It is also a boundary for permissions to resources and for billing. You are charged monthly for all resources in a subscription. A single Azure tenant (Azure Active Directory) can contain multiple Azure subscriptions.
A resource group is a container that holds related resources for an Azure solution. The resource group can include all the resources for the solution, or only those resources that you want to manage as a group.
To enable each department administrator to manage the Azure resources used by that department, you will need to create a separate subscription per department. You can then assign each department administrator as an administrator for the subscription to enable them to manage all resources in that subscription.
Reference:
https://docs.microsoft.com/en-us/azure/cost-management-billing/manage/create-subscription
https://docs.microsoft.com/en-us/azure/cost-management-billing/manage/add-change-subscription-administrator
You have an Azure environment that contains multiple Azure virtual machines.
You plan to implement a solution that enables the client computers on your on-premises network to communicate to the Azure virtual machines.
You need to recommend which Azure resources must be created for the planned solution.
Which two Azure resources should you include in the recommendation?
a virtual network gateway
a load balancer
an application gateway
a virtual network
a gateway subnet
Answers are; a virtual network gateway
a gateway subnet
To implement a solution that enables the client computers on your on-premises network to communicate to the Azure virtual machines, you need to configure a VPN (Virtual Private Network) to connect the on-premises network to the Azure virtual network.
The Azure VPN device is known as a Virtual Network Gateway. The virtual network gateway needs to be located in a dedicated subnet in the Azure virtual network. This dedicated subnet is known as a gateway subnet and must be named GatewaySubnet.
Note: a virtual network (answer D) is also required. However, as we already have virtual machines deployed in a Azure, we can assume that the virtual network is already in place.
References:
https://docs.microsoft.com/en-us/office365/enterprise/connect-an-on-premises-network-to-a-microsoft-azure-virtual-network
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
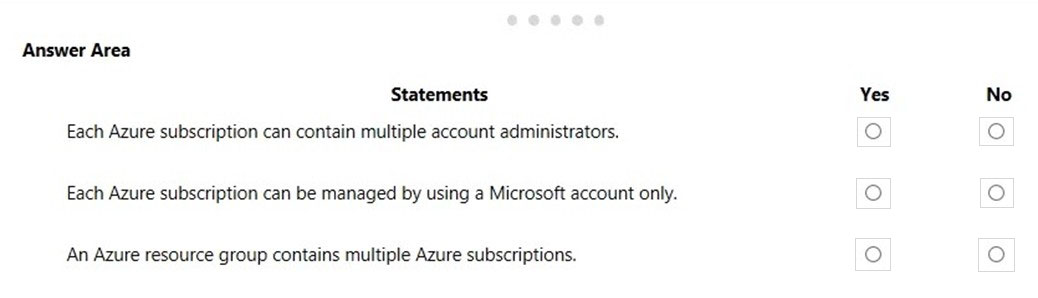
Box 1: No
You can have 1 Account Administrator and 1 Service Administrator, but you can have 200 Co-Administrators per subscription
Box 2: No
You need an Azure Active Directory account to manage a subscription, not a Microsoft account. An account is created in the Azure Active Directory when you create the subscription. Further accounts can be created in the Azure Active Directory to manage the subscription.
Box 3: No
Resource groups are logical containers for Azure resources. However, resource groups do not contain subscriptions. Subscriptions contain resource groups.
References:
https://docs.microsoft.com/en-us/office365/enterprise/subscriptions-licenses-accounts-and-tenants-for-microsoft-cloud-offerings
Your company plans to move several servers to Azure.
The company's compliance policy states that a server named FinServer must be on a separate network segment.
You are evaluating which Azure services can be used to meet the compliance policy requirements.
Which Azure solution should you recommend?
a resource group for FinServer and another resource group for all the other servers
a virtual network for FinServer and another virtual network for all the other servers
a VPN for FinServer and a virtual network gateway for each other server
one resource group for all the servers and a resource lock for FinServer
Answer is a virtual network for FinServer and another virtual network for all the other servers
Networks in Azure are known as virtual networks. A virtual network can have multiple IP address spaces and multiple subnets. Azure automatically routes traffic between different subnets within a virtual network.
The question states that FinServer must be on a separate network segment. The only way to separate FinServer from the other servers in networking terms is to place the server in a different virtual network to the other servers.
References:
https://docs.microsoft.com/en-us/azure/virtual-network/virtual-network-vnet-plan-design-arm
Your company plans to migrate all its network resources to Azure.
You need to start the planning process by exploring Azure.
What should you create first?
a subscription
a resource group
a virtual network
a management group
Answer is a subscription
The first thing you create in Azure is a subscription. You can think of an Azure subscription as an Azure account. You get billed per subscription.
A subscription is an agreement with Microsoft to use one or more Microsoft cloud platforms or services, for which charges accrue based on either a per-user license fee or on cloud-based resource consumption.
Microsoft's Software as a Service (SaaS)-based cloud offerings (Office 365, Intune/EMS, and Dynamics 365) charge per-user license fees.
Microsoft's Platform as a Service (PaaS) and Infrastructure as a Service (IaaS) cloud offerings (Azure) charge based on cloud resource consumption.
You can also use a trial subscription, but the subscription expires after a specific amount of time or consumption charges. You can convert a trial subscription to a paid subscription.
Organizations can have multiple subscriptions for Microsoft's cloud offerings.
References:
https://docs.microsoft.com/en-us/office365/enterprise/subscriptions-licenses-accounts-and-tenants-for-microsoft-cloud-offerings