AZ-305: Designing Microsoft Azure Infrastructure Solutions
You have an Azure subscription that contains a custom application named Application1. Application1 was developed by an external company named Fabrikam, Ltd. Developers at Fabrikam were assigned role-based access control (RBAC) permissions to the Application1 components. All users are licensed for the Microsoft 365 E5 plan.
You need to recommend a solution to verify whether the Fabrikam developers still require permissions to Application1. The solution must meet the following requirements:
- To the manager of the developers, send a monthly email message that lists the access permissions to Application1.
- If the manager does not verify an access permission, automatically revoke that permission.
- Minimize development effort.
What should you recommend?
In Azure Active Directory (Azure AD), create an access review of Application1.
Create an Azure Automation runbook that runs the Get-AzRoleAssignment cmdlet.
In Azure Active Directory (Azure AD) Privileged Identity Management, create a custom role assignment for the Application1 resources.
Create an Azure Automation runbook that runs the Get-AzureADUserAppRoleAssignment cmdlet.
Answer is In Azure Active Directory (Azure AD), create an access review of Application1.
An access review is a feature in Azure AD that enables an administrator to review the membership of a group or application role to ensure that only the right people have continued access. This aligns with the requirement to verify access permissions to Application1.
Access reviews can be scheduled to run on a regular basis and can be configured to send email notifications to reviewers. This satisfies the requirement to send a monthly email message to the manager of the developers listing the access permissions to Application1.
Access reviews also provide the option to automatically revoke access if the reviewer does not verify an access permission, which fulfills the requirement to automatically revoke permissions if the manager does not verify them.
Implementing an access review in Azure AD requires minimal development effort and can be set up through the Azure portal with a few simple clicks.
Reference:
https://learn.microsoft.com/en-us/azure/active-directory/governance/access-reviews-overview
You have an Azure Active Directory (Azure AD) tenant that syncs with an on-premises Active Directory domain.
You have an internal web app named WebApp1 that is hosted on-premises. WebApp1 uses Integrated Windows authentication.
Some users work remotely and do NOT have VPN access to the on-premises network.
You need to provide the remote users with single sign-on (SSO) access to WebApp1.
Which two features should you include in the solution?
Azure AD Application Proxy
Azure AD Privileged Identity Management (PIM)
Conditional Access policies
Azure Arc
Azure AD enterprise applications
Azure Application Gateway
Answers are;
A. Azure AD Application Proxy
E. Azure AD enterprise applications
It's required to download connector under (Application Proxy) and create a new application under (Enterprise Application), however for (Pre Authentication) option, you can choose "Passthrough" or "Azure Active Directory", and both will work, but it's recommended to use "Azure Active Directory" so you can take advantage of using conditional access and MFA. Answer is (A) & (E) as they're both required as part of the solution to work.
A: Application Proxy is a feature of Azure AD that enables users to access on-premises web applications from a remote client. Application Proxy includes both the Application Proxy service which runs in the cloud, and the Application Proxy connector which runs on an on-premises server. You can configure single sign-on to an Application Proxy application.
E: Add an on-premises app to Azure AD
Now that you've prepared your environment and installed a connector, you're ready to add on-premises applications to Azure AD.
1. Sign in as an administrator in the Azure portal.
2. In the left navigation panel, select Azure Active Directory.
3. Select Enterprise applications, and then select New application.
4. Select Add an on-premises application button which appears about halfway down the page in the On-premises applications section. Alternatively, you can select Create your own application at the top of the page and then select Configure Application Proxy for secure remote access to an on-premise application.
5. In the Add your own on-premises application section, provide the following information about your application.
6. Etc.
Incorrect:
Not C: Conditional Access policies are not required.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/app-proxy/application-proxy-add-on-premises-application
You have an Azure Active Directory (Azure AD) tenant named contoso.com that has a security group named Group1. Group1 is configured for assigned membership. Group1 has 50 members, including 20 guest users.
You need to recommend a solution for evaluating the membership of Group1. The solution must meet the following requirements:
- The evaluation must be repeated automatically every three months.
- Every member must be able to report whether they need to be in Group1.
- Users who report that they do not need to be in Group1 must be removed from Group1 automatically.
- Users who do not report whether they need to be in Group1 must be removed from Group1 automatically.
What should you include in the recommendation?
Implement Azure AD Identity Protection.
Change the Membership type of Group1 to Dynamic User.
Create an access review.
Implement Azure AD Privileged Identity Management (PIM).
Answer is Create an access review.
Azure Active Directory (Azure AD) access reviews enable organizations to efficiently manage group memberships, access to enterprise applications, and role assignments. User's access can be reviewed on a regular basis to make sure only the right people have continued access.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/governance/access-reviews-overview
You plan to deploy Azure Databricks to support a machine learning application. Data engineers will mount an Azure Data Lake Storage account to the Databricks file system. Permissions to folders are granted directly to the data engineers.
You need to recommend a design for the planned Databrick deployment. The solution must meet the following requirements:
- Ensure that the data engineers can only access folders to which they have permissions.
- Minimize development effort.
- Minimize costs.
What should you include in the recommendation?

Check the answer section

Recommended design for the planned Databricks deployment that meets the given requirements:
- Databricks SKU: Premium
- Premium SKU provides access control for DBFS root and FUSE mount points. This will ensure that the data engineers can only access folders to which they have permissions.
- Cluster Configuration: Credentials passthrough
- Credentials passthrough allows users to authenticate with Azure Data Lake Storage using their own Azure AD credentials. This minimizes development effort and costs, as it does not require additional Azure AD application registration and service principal management.
Therefore, the recommended design for the planned Databricks deployment is to use Premium SKU for access control of DBFS root and FUSE mount points, and to configure credentials passthrough for authentication with Azure Data Lake Storage. This design meets the requirements of ensuring data engineers can only access folders to which they have permissions, minimizing development effort and costs.
Reference:
https://docs.microsoft.com/en-us/azure/databricks/security/credential-passthrough/adls-passthrough
You plan to deploy an Azure web app named App1 that will use Azure Active Directory (Azure AD) authentication.
App1 will be accessed from the internet by the users at your company. All the users have computers that run Windows 10 and are joined to Azure AD.
You need to recommend a solution to ensure that the users can connect to App1 without being prompted for authentication and can access App1 only from company-owned computers.
What should you recommend for each requirement?
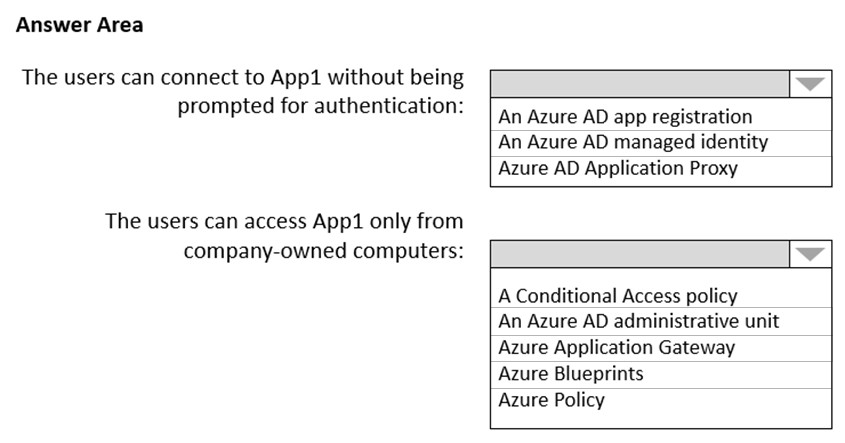
Check the answer section
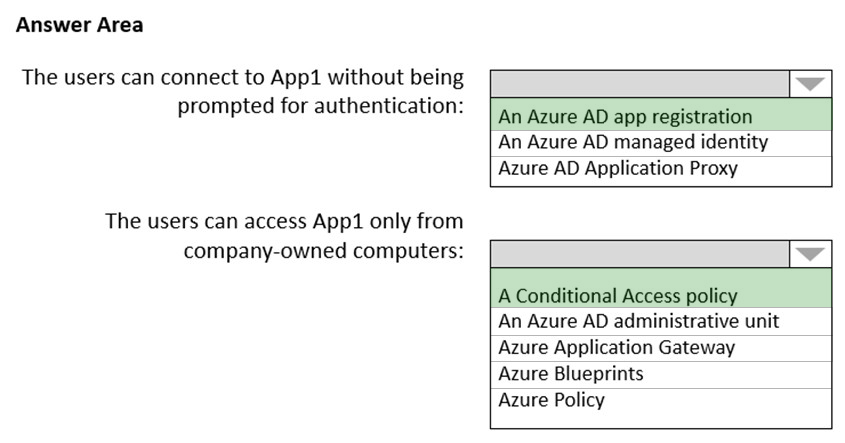
Box 1: An Azure AD app registration
Azure active directory (AD) provides cloud based directory and identity management services.You can use azure AD to manage users of your application and authenticate access to your applications using azure active directory.
You register your application with Azure active directory tenant.
Box 2: A conditional access policy
Conditional Access policies at their simplest are if-then statements, if a user wants to access a resource, then they must complete an action.
By using Conditional Access policies, you can apply the right access controls when needed to keep your organization secure and stay out of your user's way when not needed.
Reference:
https://codingcanvas.com/using-azure-active-directory-authentication-in-your-web-application/
https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/overview
https://docs.microsoft.com/en-us/azure/active-directory/manage-apps/what-is-application-management
You are designing a large Azure environment that will contain many subscriptions.
You plan to use Azure Policy as part of a governance solution.
To which three scopes can you assign Azure Policy definitions?
Azure Active Directory (Azure AD) administrative units
Azure Active Directory (Azure AD) tenants
subscriptions
compute resources
resource groups
management groups
Answers are;
C. subscriptions
E. resource groups
F. management groups
An assignment is a policy definition or initiative that has been assigned to a specific scope. This scope could range from a management group to an individual resource. The term scope refers to all the resources, resource groups, subscriptions, or management groups that the definition is assigned to. Assignments are inherited by all child resources. This design means that a definition applied to a resource group is also applied to resources in that resource group. However, you can exclude a subscope from the assignment.
Reference:
https://learn.microsoft.com/en-us/azure/governance/policy/overview#assignments
You have an Azure subscription. The subscription has a blob container that contains multiple blobs.
Ten users in the finance department of your company plan to access the blobs during the month of April.
You need to recommend a solution to enable access to the blobs during the month of April only.
Which security solution should you include in the recommendation?
shared access signatures (SAS)
Conditional Access policies
certificates
access keys
Answer is shared access signatures (SAS)
Shared access signatures for blobs, files, queues, and tables. Shared access signatures (SAS) provide limited delegated access to resources in a storage account via a signed URL. The signed URL specifies the permissions granted to the resource and the interval over which the signature is valid. A service SAS or account SAS is signed with the account key, while the user delegation SAS is signed with Azure AD credentials and applies to blobs only.
Reference:
https://learn.microsoft.com/en-us/azure/storage/common/authorize-data-access#understand-authorization-for-data-operations
https://docs.microsoft.com/en-us/azure/storage/common/storage-sas-overview
Your company deploys several virtual machines on-premises and to Azure. ExpressRoute is deployed and configured for on-premises to Azure connectivity.
Several virtual machines exhibit network connectivity issues.
You need to analyze the network traffic to identify whether packets are being allowed or denied to the virtual machines.
Solution: Use Azure Traffic Analytics in Azure Network Watcher to analyze the network traffic.
Does this meet the goal?
Yes
No
Answer is No
Azure Traffic Analytics is designed to help diagnose performance and connectivity issues in Azure virtual networks. It uses network flow data collected by Azure Network Watcher's flow logs, and provides insights into network activity and patterns. However, it does not provide the ability to identify whether packets are being allowed or denied to specific virtual machines.
IP flow verify checks if a packet is allowed or denied to or from a virtual machine. The information consists of direction, protocol, local IP, remote IP, local port, and remote port. If the packet is denied by a security group, the name of the rule that denied the packet is returned. While any source or destination IP can be chosen, IP flow verify helps administrators quickly diagnose connectivity issues from or to the internet and from or to the on-premises environment.
Reference:
https://docs.microsoft.com/en-us/azure/network-watcher/network-watcher-ip-flow-verify-overview
Your company deploys several virtual machines on-premises and to Azure. ExpressRoute is deployed and configured for on-premises to Azure connectivity.
Several virtual machines exhibit network connectivity issues.
You need to analyze the network traffic to identify whether packets are being allowed or denied to the virtual machines.
Solution: Use Azure Advisor to analyze the network traffic.
Does this meet the goal?
Yes
No
Answer is No
Azure advisor is not going to show you or help you troubleshoot connectivity problems.
IP flow verify checks if a packet is allowed or denied to or from a virtual machine. The information consists of direction, protocol, local IP, remote IP, local port, and a remote port. If the packet is denied by a security group, the name of the rule that denied the packet is returned. While any source or destination IP can be chosen, IP flow verify helps administrators quickly diagnose connectivity issues from or to the internet and from or to the on-premises environment.
Reference:
https://learn.microsoft.com/en-us/azure/network-watcher/network-watcher-ip-flow-verify-overview
Your company deploys several virtual machines on-premises and to Azure. ExpressRoute is deployed and configured for on-premises to Azure connectivity.
Several virtual machines exhibit network connectivity issues.
You need to analyze the network traffic to identify whether packets are being allowed or denied to the virtual machines.
Solution: Use Azure Network Watcher to run IP flow verify to analyze the network traffic.
Does this meet the goal?
Yes
No
Answer is Yes
Azure Network Watcher IP Flow Verify allows you to detect traffic filtering issues at a VM level.
IP flow verify checks if a packet is allowed or denied to or from a virtual machine. The information consists of direction, protocol, local IP, remote IP, local port, and remote port. If the packet is denied by a security group, the name of the rule that denied the packet is returned. While any source or destination IP can be chosen, IP flow verify helps administrators quickly diagnose connectivity issues from or to the internet and from or to the on-premises environment.
Reference:
https://docs.microsoft.com/en-us/azure/network-watcher/network-watcher-ip-flow-verify-overview